User Tools
Sidebar
This is an old revision of the document!
Firewall
The Firewall page allows you to configure options to protect/facilitate certain network communications.
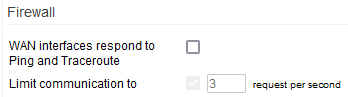
WAN interfaces respond to ping and traceroute - If enabled, allows your device to reply to certain ICMP/UDP packets from Internet hosts so that ping and traceroute will work from the Internet.
Limit communication to - Specifies the maximum number of requests per second to which the Firewall will reply. Setting a limit number is recommended to prevent DDoS attacks.
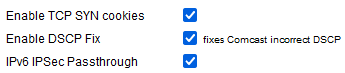
Enable TCP SYN cookies - Enabling this protects the router from SYN Flood attacks via the well-known “SYN cookies” technique. This function encodes information from the SYN packet into the response (SYN/ACK). Despite being a standard technique, enabling this will create some secondary limitations that may not be handled well by some old TCP/IP stacks.
Enable DCSP Fix - This enables a workaround for a well-known issue related to DSCP (packet marking) when connected to the Comcast ISP.
IPv6 IPSec Passthrough -
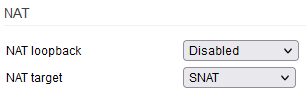
NAT loopback - also known as “Hairpinning”, this technique allows LAN devices to access another LAN device via the WAN interface of your router. This is common practice, for example, when connecting to the DDNS domain of your router from the LAN (for administration purposes). This legacy setting is rarely, if ever needed nowadays. It also can create a bottleneck on fast connections.
- All
- Forwarded Only
- Disabled
NAT target - Defines the way NAT is implemented for the sake of Hairpinning. Masquerade is the default, however this involves an additional lookup ad the mapping of done towards an interface. SNAT is minimally minutely faster as the NAT mapping points directly to the destination IP and so it bypasses the lookup stage.
Enable IGMP proxy - Runs the IGMP (Internet Group Management Protocol) service on the router.
LAN0/LAN1/LAN2/LAN3 - Specifies which bridges will be subscribed to partecipate in IGMP using the router as a proxy between the LANs selected. Essentially, this allows IGMP to work between VLANs.
Enable quick leave - This is a feature of IGMP v2. This allows the router to stop the streaming of a multicast to an IP address as soon as that end device sends the quick leave IGMP packet.
Custom Configuration - This option allows you to set up advanced parameters for the IGMP proxy daemon. Please consult the official IGMP documentation before finalizing these settings.
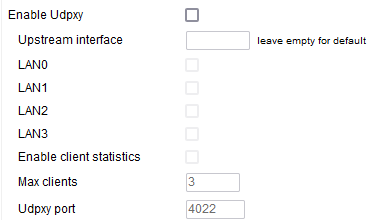
Enable Udpxy - Like IGMP proxy, Udpxy allows multicast communications between senders and receivers in different VLANs. Since their behavior is almost identical, it is recommended you use either Udpxy or IGMP proxy, but not both at the same time.
Upstream interface - Defines where the stream source is expected to live. (Default: blank).
LAN0/LAN1/LAN2/LAN3 - This is where the stream clients are expected to live.
Enable client statistics - Enabling this causes FreshTomato to collect statistical information about Udpxy clients.
Max clients - Considering this is a lightwave protocol it works well for a limited number of clients, you might want to impose a maximum number.Specifies the maximum number of simultaneous Udpxy clients.
Udpxy port- This is where you can consult the Udpxy information on your router.

Efficient Multicast Forwarding (IGMP Snooping) - IGMP snooping is a way to have the switch (router) facilitating the discovery of multicast (IGMP) clients. Beware that enabling IGMP snooping might interfere with some multicast-based applications/protocols. This issue is well-known, for example when using uPnP (Universal Plug 'n Play).
Force IGMPv2 - IGMPv2 enhances the IGMP communication supporting additional messages/behavior to optimise the end-to-end communication between client and server. Possibly the most important being the “Group Leave” message which is lacking instead in IGMP v1.