User Tools
Sidebar
Firewall
The Firewall page allows you to configure options to protect or facilitate various types of network communications.
Firewall
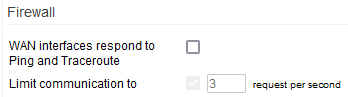
WAN interfaces respond to ping and traceroute: lets your device reply to ping/traceroute request packets from Internet hosts.
This is needed for ping and traceroute to work via the Internet. It also may be needed for proper functioning of some VPN or IPv6 protocols.
Limit communication to: specifies the maximum number of requests per second to which the Firewall replies.
Setting a limit is recommended to prevent DDoS attacks.
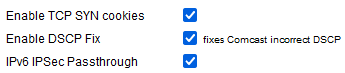
Enable TCP SYN cookies: uses “SYN cookies” to protect the router from SYN Flood attacks.
It encodes information from the SYN packet into the (SYN/ACK) response. It is a standard method for preventing SYN floods. However, it has limitations that may cause issues with some old TCP/IP stacks.
Enable DCSP Fix: enables a workaround for packet marking, a well-known DCSP issue when using Comcast.
Allow DHCP Spoofing: makes FreshTomato accept/process packets from DHCP servers with different IP than the one it advertises.
Such behaviour is often categorized as a DHCP spoofing attack, but rarely, might be legitimate. Using this lowers security.
Smart MTU black hole detection: this feature detects ICMP black holes and smartly tries to adjust the path MTU.
For details on MTU and black holes, see this blog post: The CloudFlare Blog: Path MTU Discovery in Practice
NAT
NAT loopback: lets LAN devices access each other via the router's WAN interface.
Also known as “Hairpinning”, it's often used when connecting to the DDNS domain of your router via the LAN. These days, this setting is almost never needed. Also, it can create speed bottlenecks.
- All
- Forwarded Only
- Disabled
NAT target: defines how NAT is implemented in loopback situations.
Masquerade is the default, but involves an additional lookup, and the mapping is done towards an interface. SNAT is minutely faster, as its NAT mapping points directly to the destination IP, thus bypassing the lookup stage. However, SNAT is less reliable than Masquerade.
Multicast
Enable IGMP proxy: enables the Internet Group Management Protocol service.
LAN0 - LAN3 specify which bridges will participate in IGMP, with the router acting as a proxy between chosen LANs. This lets IGMP work between VLANs.
- LAN0 - Causes the LAN0 bridge to join in IGMP proxy.
- LAN1 - Causes the LAN1 bridge to join in IGMP proxy.
- LAN2 - Causes the LAN2 bridge to join in IGMP proxy.
- LAN3 - Causes the LAN3 bridge to join in IGMP proxy.
Enable quick leave: this IGMPv2 feature lets the router stop multicasting to an IP that has sent it a “quick leave” packet.
Custom Configuration: lets you configure advanced settings for the IGMP proxy daemon. Consult official documentation.
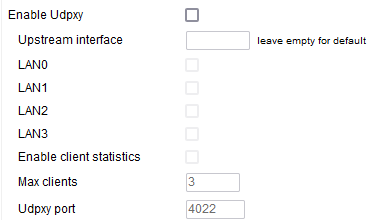
Enable Udpxy: like IGMP proxy, this lets devices on different VLANs do multicast communications.
Since they are similar, use one or the other, but not both at the same time.
Upstream interface: here, enter the expected stream source location.
(Default: blank).
LAN0/LAN1/LAN2/LAN3 - specifies the location streaming clients should be found.
Enable client statistics: causes FreshTomato to collect statistics about Udpxy clients.
Max clients: the maximum number of simultaneous Udpxy clients.
Udpxy is is a lightweight protocol, so it works well for a limited number of clients. You might want to set a maximum limit.
Udpxy port: specifies the port on which to receive Udpxy information from your router.

Efficient Multicast Forwarding (IGMP Snooping): IGMP snooping makes the router's switch facilitate discovery of Multicast IGMP clients. This helps to send multicast traffic only towards ports with at least one multicast subscriber, reducing overall multicast traffic.
However, caution is advised. IGMP Snooping can interfere with functioning of UPnP or DLNA. This can make Multicast configuration errors or deficiencies appear as UPnP issues. Enabling IGMP snooping on a router's switch interferes with UPnP/DLNA device discovery. Specifically, it can interfere with SSDP protocol transmissions. If IGMP snooping is improperly configured (say, without an active querier/IGMP proxy), it can make UPnP appear unreliable.
A common symptom of this is a network host (say, a Smart TV) which appears after it's powered on, but then “disappears” from the network after a few minutes. To be more precise, typically 30 minutes. This is because the default setting for when IGMP group membership will expire. Please be aware of the wireless multicast forwarding setting in the the Advanced/Wireless menu.
Force IGMPv2: forces IGMPv2 to be used on the network.
IGMPv2 enhances IGMP with additional messages/behavior to optimize end-to-end client-server communication. Probably the most important one is the “Leave Group” message. When a host wants to stop listening to a multicast group address, it reports to the router that it has stopped listening. In v1, the host simply stopped listening, without informing the router.
Other features of IGMPv2 include:
Group specific membership query: Now, the router can send a membership query for a specific group address. When the router receives a leave group message, it will use this query to check if there are still hosts interested in receiving the multicast traffic.
MRT (Maximum Response Time) field. This new field in query messages specifies how much time hosts have to respond to the query.
Querier election process. When two routers are on the same subnet, only one should send query messages. Having an “election” process ensures only one router, with the lowest IP address, becomes the active querier.