User Tools
Sidebar
Table of Contents
Enable Password-less Router-to-Router SSH Encryption
Overview
This setup allows a primary router, (the “SSH Client”) to control a secondary router (the “SSH Host”), from the command-line, through an encrypted (tunnel) connection.
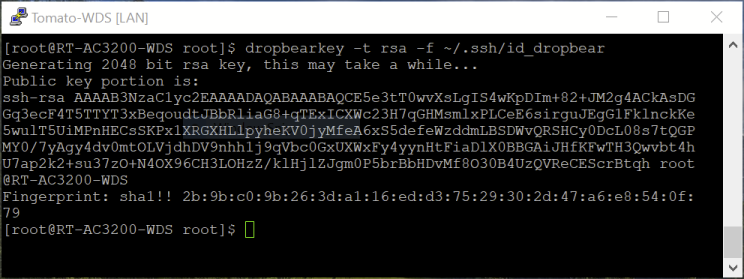
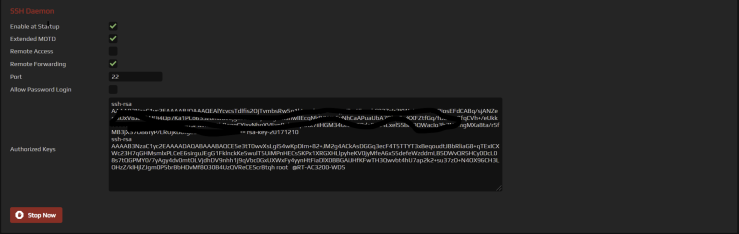
FreshTomato includes Dropbear, an SSH client/server program. Dropbear can generate an encryption KeyPair that offers passwordless connections. A command is run on the primary router which generates a public key. That Public Key must then be entered into the secondary router’s Authorized Keys field, in the SSH Daemon section of the Admin Access menu.
This can be useful, for example:
- When the the secondary router system doesn't maintain a system clock,
and time-sensitive jobs must be scheduled. - For running scripts on the secondary router using supported commands.
- As seen below, for switching wireless radio(s) on/off on a schedule (not shown).
Setting up/Establishing a Tunnel
Follow these steps to generate a Keypair and establish an SSH tunnel:
- In the above screenshot, a pre-existing, unrelated key was redacted.
- Now, connect to the secondary router via SSH (running on the primary router).
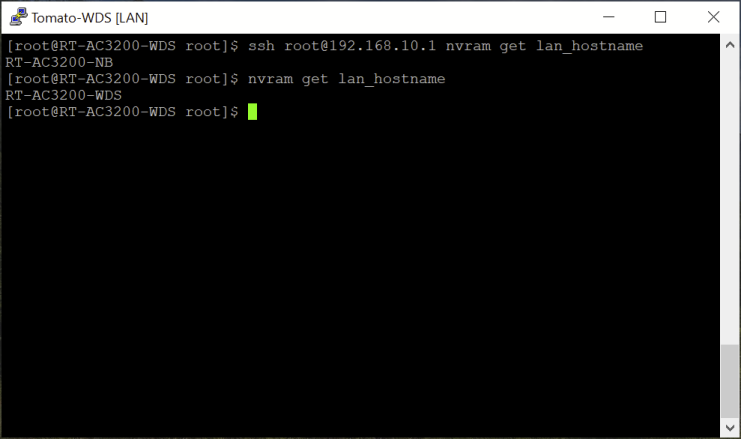
The example below uses the nvram command to display the hostname.
The first command string (“ssh root@192.168.10.1 nvram get lan_hostname”)
executes the command on the secondary router and then
it [“nvram get lan_hostname”] is executed locally, on the primary router.
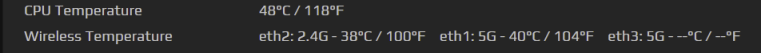
Usage Example
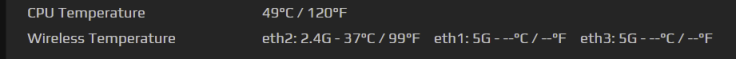
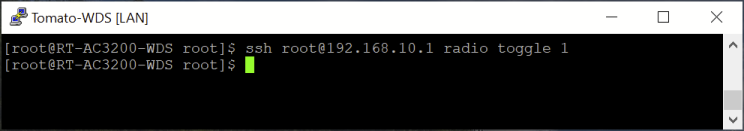
This example enables/disables the secondary router's eth1 5Ghz WiFi interface. (Temperature is shown only when the interface is enabled).
Since “radio toggle 1” is a toggle switch, if the same command is repeated, the eth1 interface will be disabled on the primary router.
Passwordless Router-to-Router SSH Notes
- The SSH daemon must be enabled on both routers.
- The key generated will be erased after a reboot of the Primary router.
- Either keep a copy of the “id_dropbear” file offline (on a flash drive,
or CIFS Client share) for restoration or; - Be prepared to repeat (steps 1. and 2.) after a reboot, removing
any redundant key from the secondary router.
This guide was produced using PuTTY v0.76 and FreshTomato r2021.5.
Inspiration was provided by this article. The process was first documented here.