User Tools
Sidebar
Table of Contents
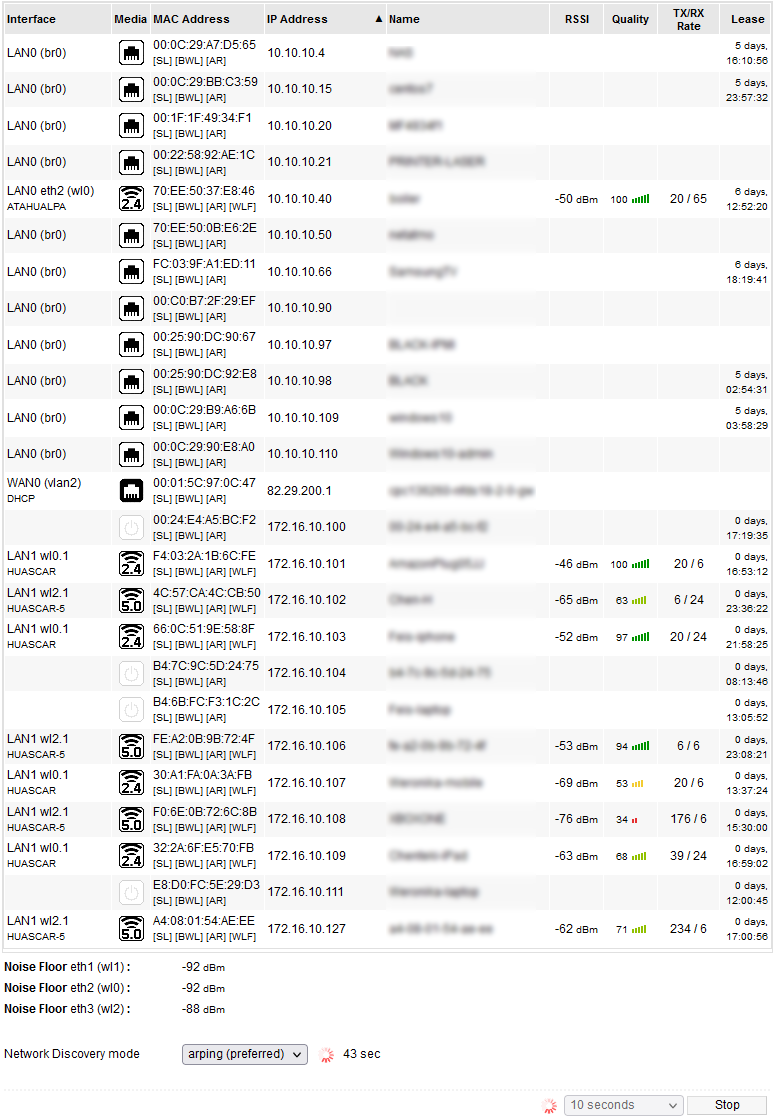
Device List
The Device List menu displays an overall view of the devices connected to your LAN.
Information is gathered from several sources, including DHCP leases, ARP tables, and WiFi clients.
Interface: lists the interface on which the router sees the device.
Since r2021.3, this includes the physical/logical interface name and WiFi SSID.
- brX - is a bridge representing the LAN.
- ethX - is an Ethernet physical interface. This name might be used
directly, or it might be used indirectly if a bridge/PPP/VPN connection
is associated with the interface.
- pppX - is a Point-to-Point Protocol interface, usually on the WAN.
- vlanX- is a virtual interface, always related to a physical interface.
For example, in the above example, “vlan2” represents a WAN interface.
- wlX - is a (main) wireless radio interface.
- If you have Virtual Wireless set up, you may have several
of these, depending on the number of radios in your router. - Virtual wireless interfaces are named as wlX.Y .
Devices connected via WiFi appear under the interface name of the connection's SSID.
Device names start at “0”. The first WiFi adapter might be named “wl0”. The second might be “eth1”.
When virtual interfaces are created (secondary SSIDs), additional instances are created.
Media: an icon here represents the interface on which the device is connected, and its connection status.
Interface types include:
- Ethernet
- WiFi (2.4GHz)
- WiFi (5GHz)
- Cellular 3G/4G/5G ISP connection
- PPPoE connection to ISP
- Wireless client (to another router/AP)
- Wireless bridge (to another router/AP)
- PPTP client
A WAN interface shows with black and white inverted.
A greyed-out power icon is an off or disconnected device.
Clicking on a greyed out device icon will wake the device.
You will then be prompted to confirm you want to wake the device.
For WoL to work, the client also must support it. Also, WoL settings in the BIOS, network adapter and OS may need adjusting.
MAC Address: the hardware address associated with the interface.
- Clicking a MAC address runs a search to identify the device
vendor, based on its device OUI (OUI).- The OUI is derived from the first 6 digits of its MAC address.
- This functions only for factory-programmed MAC addresses.
- It won't work with manually-configured MAC addresses,
as they can be arbitrarily assigned.
- [DR] stands for the DHCP Reservation feature.
- This forwards you to the DHCP Reservation menu
where you can assign a reservation to the MAC address. - While there, checking Bound to will enable static ARP mapping
to the MAC address. This protects against ARP spoofing.
- [BWL] forwards you to the Bandwidth Limiter menu. There, you
can limit the bandwidth of the device with this MAC address.
- [AR] forwards you to the Access Restriction menu,
where you can restrict the device's WAN communications.
- [WLF] forwards you to the Wireless Filter menu. There,
the device's MAC address is prefilled and can be blocked from
or allowed to connect via WiFi.
IP Address: displays the address linked to the client MAC address.
Unknown addresses aren't shown. This can occur briefly while authenticating, even for WiFi clients with the correct passkey.
Name: the client device's DHCP Hostname.
If no name is shown, the device got a lease from another router, or this router rebooted after a lease was given. As a workaround, add a dhcp-host reference in dnsmasq Custom Configuration.
For example, dhcp-host=70:EE:50:37:E8:46,myhostname
This field is also affected by the “Generate a name for DHCP clients which do not otherwise have one” setting in DHCP/DNS/TFTP.
RSSI: shows Relative Signal Strength.
This applies only to this router's WiFi clients. It's measured in negative numbers, with “0” as the best value. -53 is a stronger signal than -74.
Quality: similar to RSSI, but also considers factors like noise floor/interference.
Quality is a better signal assessment.
TX/RX Rate: the current transmit/receive link speed between router/WiFi client.
These fluctuate based on client traffic level and signal quality/distance.
Lease: displays the remaining time of the DHCP lease.
Clicking this deletes the WiFi device lease and deauthorizes it. A new, manually-set static reservation address will replace the last auto-assigned address.
You will then be prompted to confirm you wish to delete the lease.
Noise floor: show the amount of interference affecting each physical radio interface.
Noise, like RSSI, is measured in negative numbers. The best possible value is -100dBm. Interference may increase this value and decrease Quality.
A strong RSSI and Noise floor may make WiFi unusable. Usually, this is caused by other WiFi gear on the same channel. Check with the Wireless Survey tool.
On the 2.4GHz band, common interference sources include:
- Bluetooth devices
- Cordless phones
- Wireless headphones
- Low-quality power supplies
- Microwave ovens
Typically, the 5GHz band has less interference.
DFS (Dynamic Frequency Selection) is a common source of interference for certain channels. DFS lets 5GHz WiFi use frequencies reserved for radar. Ironically, it was designed to reduce interference. DFS interference varies with equipment location. If you suspect interference, see Wikipedia's List of WLAN Channels for details.
Measure: an extra button on certain (mostly MIPS-based) devices to trigger Noise Floor measurement (interference).
For details about noise floor, see the Wireless Survey menu.
Network Discovery
Recent versions of Network Discovery used to collect data for Device List have been improved. Since r2021.4, (Discovery v1.7 - 2.0) scans all LAN addresses in the interface's network/netmask.
Releases since r2025.1 include v2.57 of Discovery. This adds WAN scanning and tweaks to allow better/deeper scanning. It also excludes addresses of devices already in the scan list, or those with a static MAC address. This optimizes scanning activity.
When enabled, discovery runs continuously until turned off or until you leave the Device List menu. A global page refresh is required to make elements appear/disappear automatically in the List.
(Default: off).
v2.57 also introduced a control for concurrent probes. If discovery is launched while another discovery process is running, the second discovery is skipped. On the other hand, if discovery is ongoing and an option change triggers a second run, this will force the killing of the existing discovery and impose a new execution with the changed options.
Sanitize result: clears IP neighbour/ARP table content of spurious information.
Neighbouring devices in a FAILED/INCOMPLETE state are removed immediately after a scan. However, with this option enabled, neighbouring devices in a STALE, DELAY or PROBE state are removed too. Removal is performed after a period defined by (Max Probes * 30ms).
Max Probes: defines how many concurrent probes are allowed at any given time.
If this value rises above its limit, a 250ms delay occurs before forking additional probes. A value too high might complete discovery quickly, but might also affect device performance/system stability. A low value uses less resources but will delay discovery completion time. The limit is considered globally at a systemic level, not per interface. (Default: 60).
Scan Target: defines on which interfaces devices should be probed.
Options include:
- LANs *
- WANs
- LANs and WANs
These are categories. You cannot select specific interface names.
Each interface has a hardcoded minimum of netmask /22 for each interface (or 1022 IP addresses) due to hardware/processing restrictions. Thus, if a local interface had discovery enabled, but its netmask were /21 or less, it would not be scanned.
Scan Mode: sets the scanning method used to populate Device List.
- arping - the preferred option for scanning as it's fast and doesn't
produce spurious neighbour records. This is fine in the great majority of cases.
- traceroute - might occasionally be needed. Some old Apple devices
appear only when this method is used. However this creates spurious
device neighbour cache records, so the sanitize option is recommended
when using this method.
- netcat (nc) - as with traceroute, this generates spurious neighbouring entries.
The sanitize option corrects for this. This is a good alternative method
when devices otherwise fail to be seen.
- all (round-robin) - alternates sequentially: arping, then traceroute
and then netcat at each consecutive discovery run.
The nonadjustable countdown timer near Scan Mode shows how often the scan runs. It reflects ARP cache aging time, and may vary (say, between ARM and MIPS devices).
Scan Mode options save/execute as soon as they're selected. Settings are saved in browser cookies. Your browser will remember them.
Network Discovery will likely detect modern WiFi devices connected but in sleep mode. However, their Hostname details may not display until they wake up.
Debugging:
In the remote case that the discovery does not perform as expected, it's possible to manually set the relevant NVRAM variable:
nvram set discovery_debug=1
Once set, the next discovery call will generate troubleshooting information inside the file: “/tmp/discovery.debug”.
However, it is recommended to leave this NVRAM variable unset during normal operations.
nvram unset discovery_debug
Device List Notes and Troubleshooting
- Due to it's nature, a device defined with a static ARP binding (DHCP Reservation/Static Arp option) will appear in the device list as connected even if it's not switched on or not present. It is very hard to determine if such a device is really up because you might not know on which protocol and port it is listening and ping and traceroute response may have been disabled. Luckily there are very few use cases for static ARP binding. Caution is advised.